Setting up OPNSense with Samba LDAP Authentication
Prepping the LDAP / AD Groups and Users
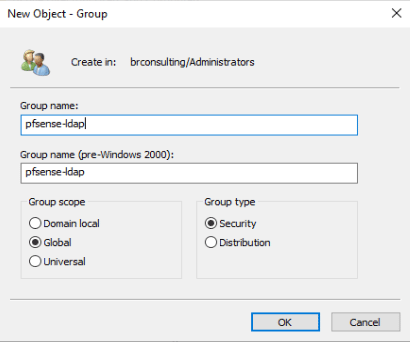
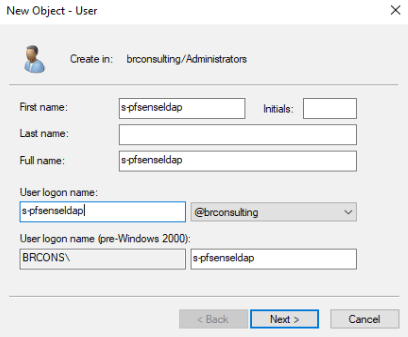
Create a group for your OPNSense to authenticate against on the LDAP server, and a user without privileges and/or interactive login for the firewall to do the ldap tree search. In this case I’ll re-use my old “pfsense-ldap” group but you should probably name it opnsense-ldap or something to your liking.
Setting up the LDAP / AD authentication in OPNSense
Once you’ve done that log into your OPNSense and do the following:
Head over to the OPNSense System → Access → Servers Section.
Then click the + icon to add an Authentication Server.
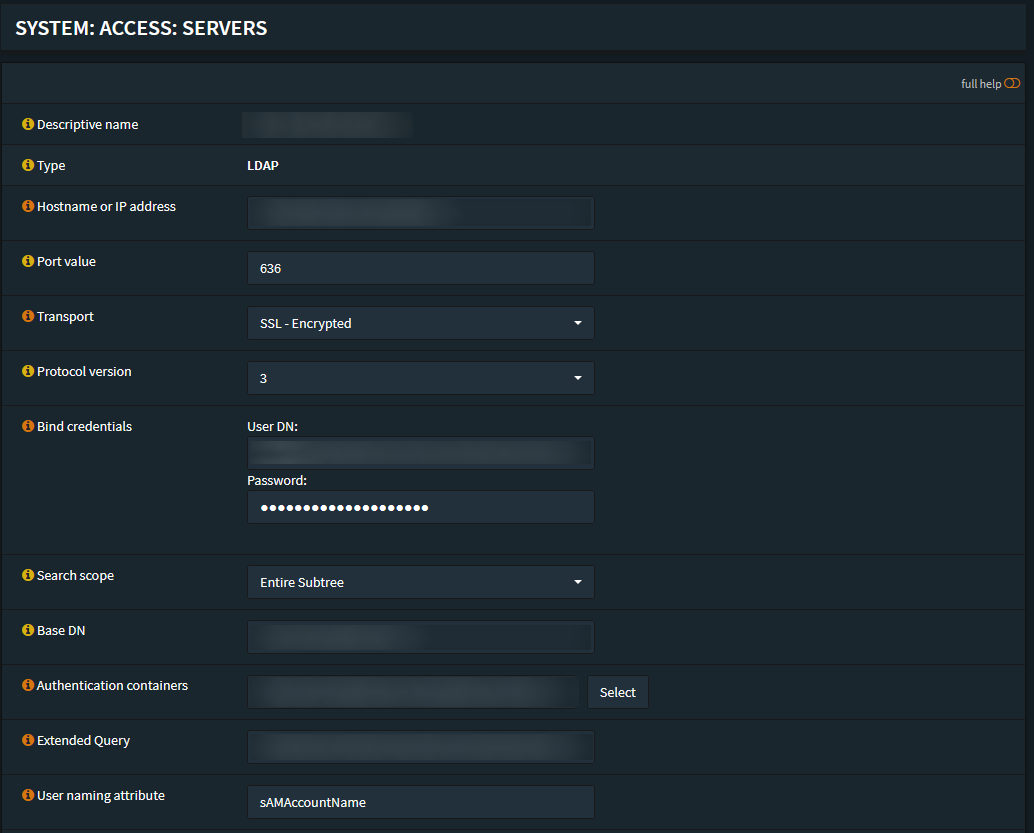
Server Settings
On the Server settings area, perform the following configuration:
- Description name: SAMBA LDAP
- Type: LDAP
Parameters
Hostname or IP address: [yourLDAPserverIPorHostname]
Port value: 389 (PLAIN LDAP) / 636 (LDAP over SSL/TLS)
Transport: TCP - Standard / SSL - Encrypted
Search scope:
- Level: Entire Subtree
- Base DN: dc=your,dc=domain,dc=com
Authentication Containers: OU=Administrators,DC=your,DC=domain,DC=com
Extended query: ENABLED
Query: memberOf=CN=opnsense-ldap,OU=Administrators,DC=your,DC=domain,DC=com
Bind anonymous: DISABLED
Bind credentials: CN=s-opnsenseldap,OU=Service Accounts,DC=your,DC=domain,DC=com
User naming attribute: samAccountName
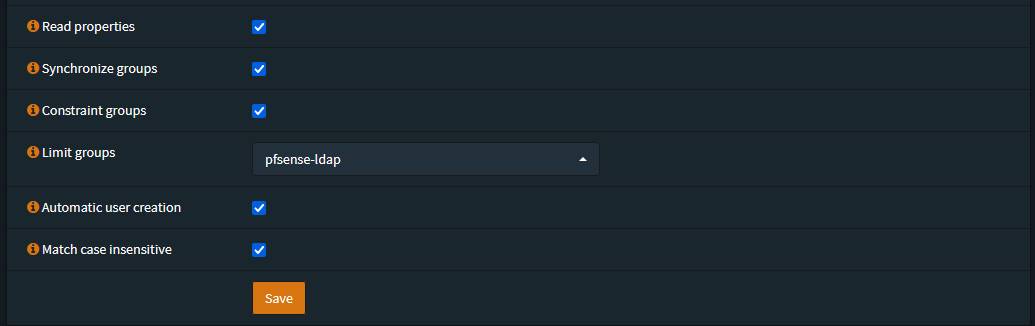
Read Properties: True
Synchronize Groups: True
Constraint Groups: True
Limit Groups: opnsense-ldap
Automatic User Creation: True
Match Case Insensitive: True
Example:
Now go to System → Access → Tester
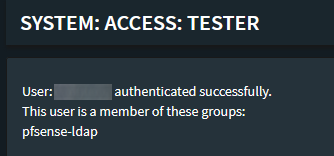
Test your LDAP login with a user that’s in the OPNSense-ldap group.
Giving permissions to your LDAP / AD Group
Once you’ve tested that successfully you can go to System → Access → Groups
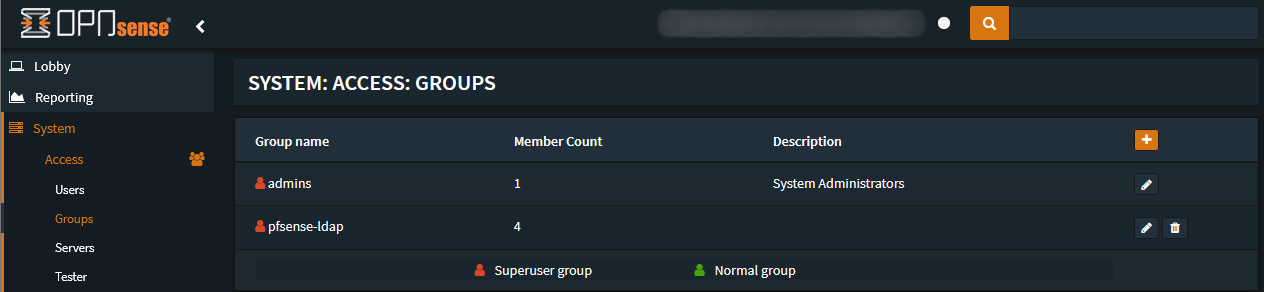
Create a group with the following settings:
- Group name: OPNSense-ldap
- Description: Samba LDAP Auth Group
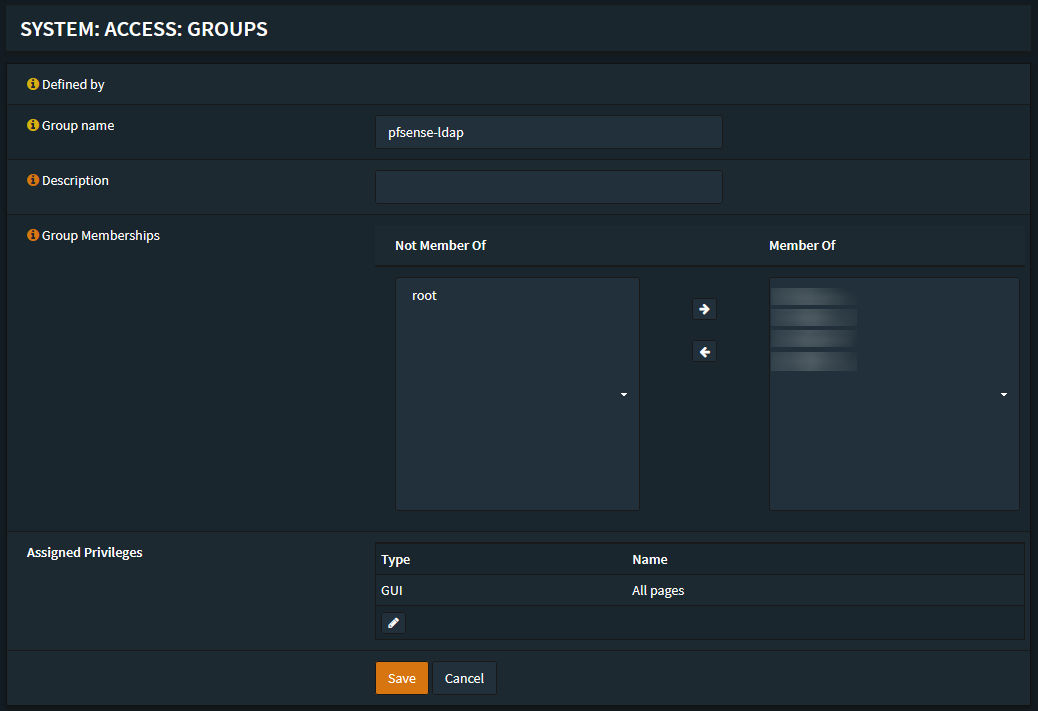
After that change/edit the permissions of the OPNSense-ldap group and add the
GUI - All Pages permission.
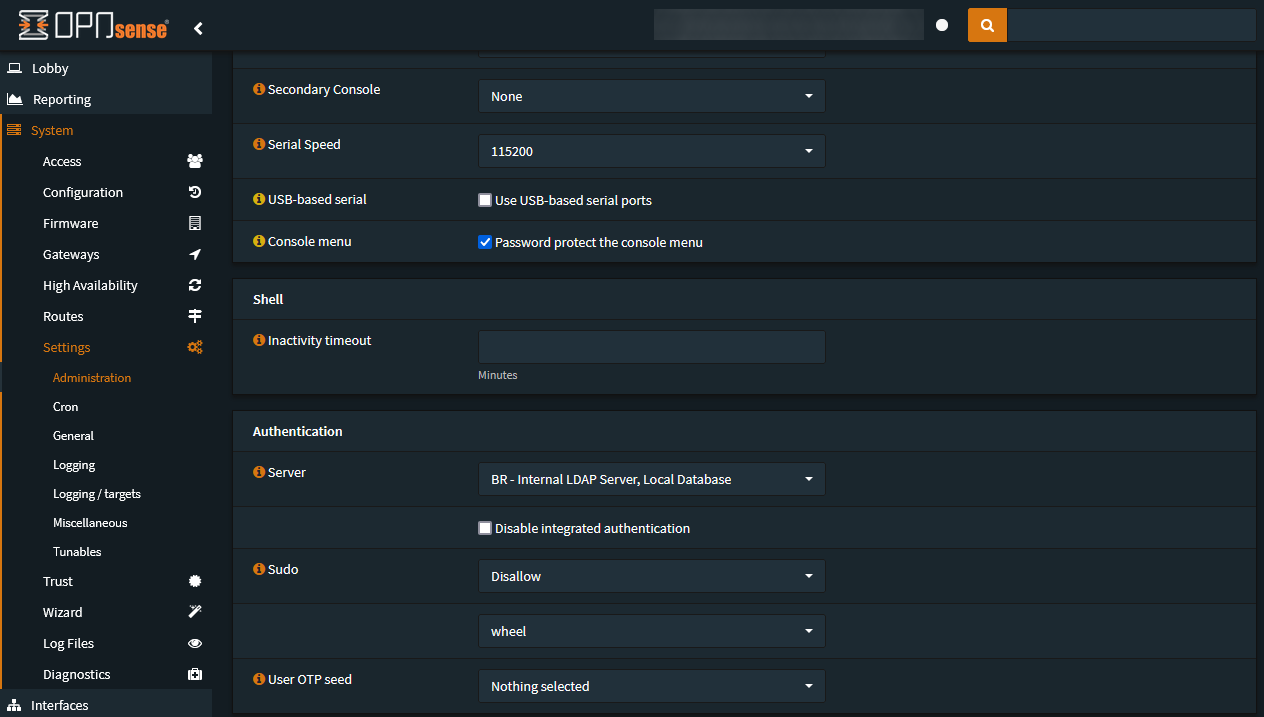
Enable the LDAP / Active Directory Authentication
Go to the System → Settings → Administration section and select your SAMBA LDAP
authentication server.
Log off the admin user and log in with your own LDAP / AD User.