Setting up pfSense with Samba LDAP Authentication
Prepping the LDAP / AD Groups and Users
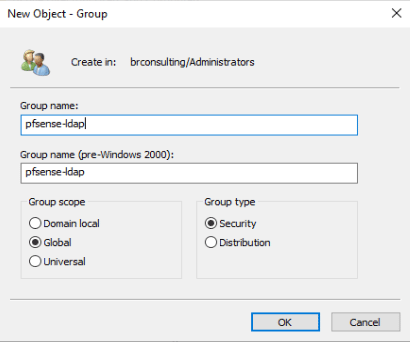
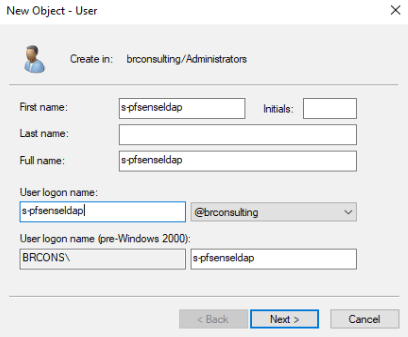
Create a group for your pfSense to authenticate against on the LDAP server, and a user without privileges and/or interactive login for the firewall to do the ldap tree search. In my case I’ll name it “pfsense-ldap”.
Setting up the LDAP / AD authentication in pfSense
Once you’ve done that log into your pfsense and do the following:
Access the Pfsense System menu and select the User manager option.
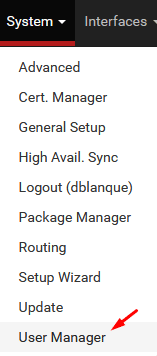
On the User manager screen, access the Authentications servers tab and click on the Add button.
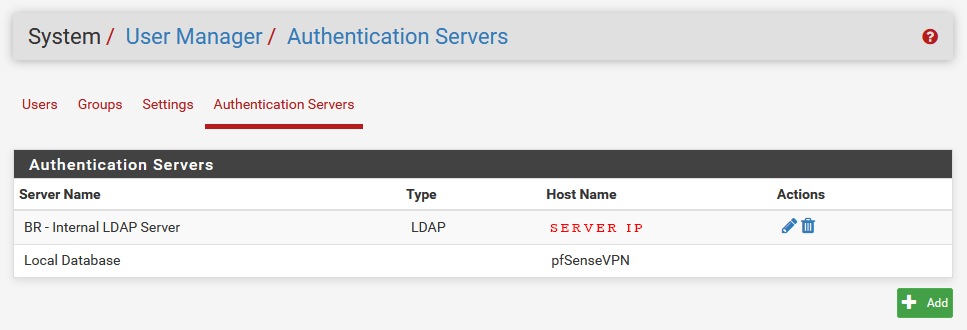
On the Server settings area, perform the following configuration:
- Description name: SAMBA LDAP
- Type: LDAP
Use the following settings:
Hostname or IP address: [yourLDAPserverIP]
Port value: 389
Transport: TCP - Standard
Peer Certificate Authority: Global Root CA List
Protocol version: 3
Server Timeout: 25
Search scope:
- Level: Entire Subtree
- Base DN: dc=your,dc=domain,dc=com
Authentication Containers: OU=Administrators,DC=your,DC=domain,DC=com
Extended query: ENABLED
Query: memberOf=CN=pfsense-ldap,OU=Administrators,DC=your,DC=domain,DC=com
Bind anonymous: DISABLED
Bind credentials: CN=s-pfsenseldap,OU=Service Accounts,DC=your,DC=domain,DC=com
User naming attribute: samAccountName
Group naming attribute: cn
Group member attribute: memberOf
RFC 2307 Groups: DISABLED
Group Object Class: posixGroup
UTF8 Encode: DISABLED
Username Alterations: DISABLED
Now go to Diagnostics → Authentication
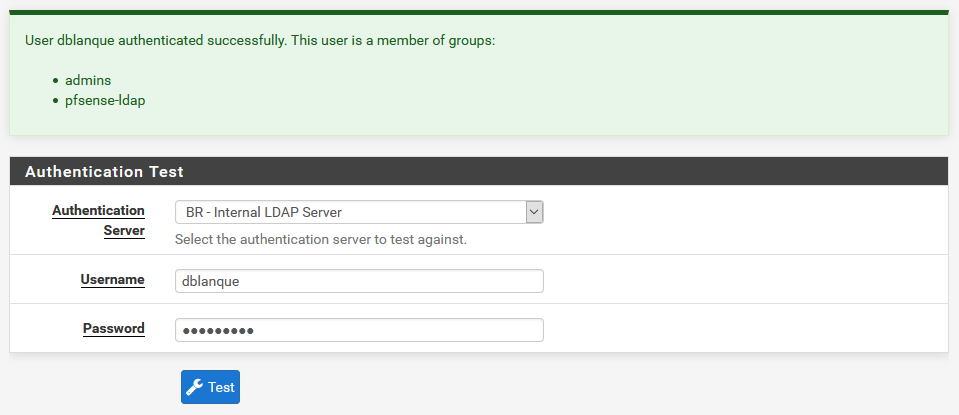
Test your LDAP login with a user that’s in the pfsense-ldap group.
Giving permissions to your LDAP / AD Group
Once you’ve tested that successfully you can go back to the User Manager (Groups Section)
Create a group with the following settings:
- Group name: pfsense-ldap
- Scope: Remote
- Description: Samba LDAP Auth Group
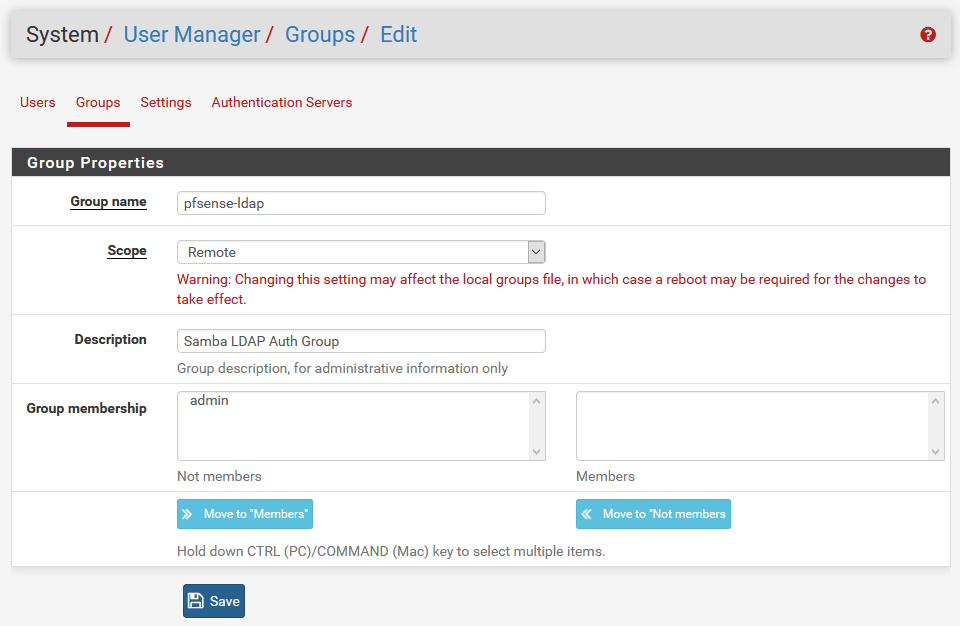
After that change/edit the permissions of the pfsense-ldap group
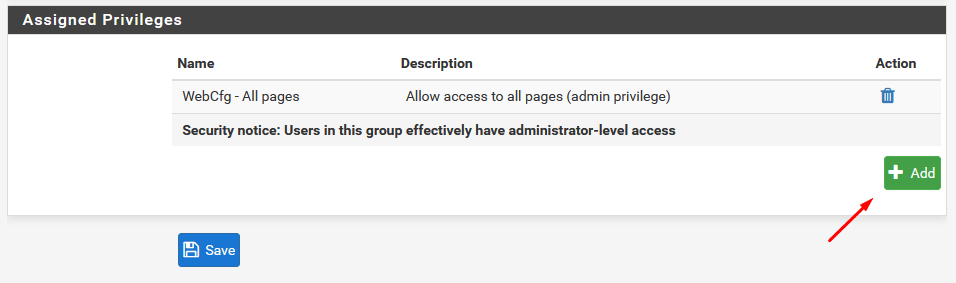
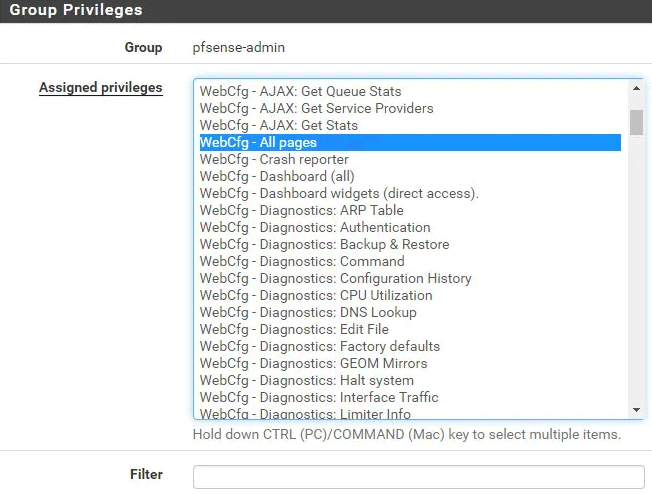
Enable the LDAP / Active Directory Authentication
Go to the User Manager / Settings section: Select the SAMBA LDAP authentication server.
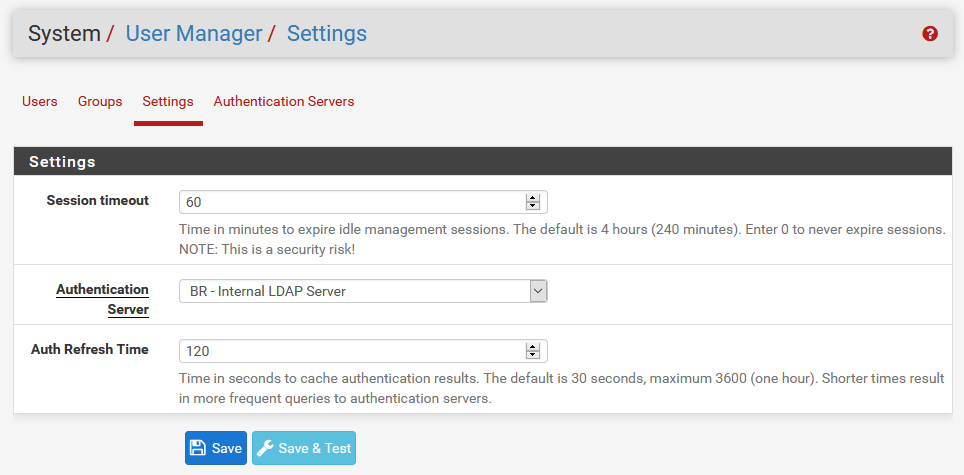
Log off the admin user and log in with your own LDAP / AD User.